Which Two Statements Describe Access Attacks
This can be combined with other direct attacks on the network as part of a coordinated attempt to prevent the network. Which two statements describe access attacks.

Ccna Cybersecurity Operations Version 1 1 Cyberops Chapter 10 Exam Answers 2019 Premium It Exam Answers
One computer accepts data packets based on the MAC address of another computer.

. One computer accepts data packets based on the MAC address of another computer. Prevention of unauthorized use of a resource. To detect listening services port scanning attacks scan a range of TCP or UDP port numbers on a host.
This sort of attack prevents an administrator from remotely accessing switch management functions. A network consisting of two or more autonomous networks c. Protection against the unauthorized disclosure of data.
Which two statements describe access attacks. The same way a professional hacker spends all day modifying hacking techniques and looking for networks to exploit. It is a framework for security policy development.
Firstly for an attacker to. Choose two Password attacks can be implemented using brute-force attack methods Trojan Horses or packet sniffers. Consider the following access list.
Choose two Select one or more. What is a characteristic of TACACS. Trust exploitation uses granted privileges to access unauthorized material.
An attacker sends an enormous quantity of data that a server cannot handle. Which statement best describes an indicator of compromise IoC. Access listaccess-list 100 permit ip host 192168101 any access-list 100 deny icmp 192168100 000255 any echo access-list 100 permit ip any any Which two actions are taken if the access list is placed inbound on a router Gigabit Ethernet port that has the IP address 19216810254 assigned.
Rootkit gains privileged access to a machine while concealing itself Spyware collects information from a target system Adware delivers advertisements with or without consent Bot waits for commands from the hacker Ransomware holds a computer system or data captive until payment is receivedent. Network Access Attacks. Up to 24 cash back 8.
Are intended to counter security attacks. Which two organizations are examples of a threat intelligence service that serves the wider security community. Choose three a payload an enabling vulnerability a propagation mechanism Which two statements describe access attacks.
A list of network devices that are known to be. A global commercial TCPIP network d. An attacker views network traffic to learn authentication credentials.
Which statement best describes access control. Which two AAA access method statements are true. Protection against denial by one of the parties in communication.
It is a standard-based model for developing firewall technologies to fight against cybercriminals. Which of the following statements best describes an intranet. It is a standard-based model for developing firewall technologies to fight against cybercriminals.
Technology is forever evolving so is hacking. Telnet DoS attack In this attack the attacker exploits a flaw in the Telnet server software running on the switch that renders the Telnet service unavailable. Password a dictionary is used for repeated login attempts.
Which statement describes a distributed denial of service attack An attacker views network traffic to learn authentication credentials. It might come as a surprise to many that as one wakes up in the morning and prepares for work gets to the office and spends nine to twelve hour working. A network that services a single company b.
Distinct enterprise networks which are connected through the Internet for the exchange of products services and business. Choose two Port redirection attacks use a network adapter card in promiscuous mode to capture all network packets that are sent across a LAN. Which access attack method involves a software program that attempts to discover a system password by the use of an electronic dictionary.
An attacker builds a botnet comprised of zombies. Choose two Trust exploitation attacks often involve the use of a laptop to act as a rogue access point to capture and copy all network traffic in a public location such as a wireless hotspot. What are the three major components of a worm attack.
An attacker builds a botnet comprised of zombies. It is an ongoing effort to protect Internet. Choose two Buffer overflow attacks write data beyond the allocated buffer memory to overwrite valid data or to exploit systems to execute malicious code.
Which statement describes a distributed denial of service attack An attacker sends an enormous quantity of data that a server cannot handle. The five types of access attacks include the following. Which two statements describe access attacks.
Assurance that the communicating entity is the one claimed. An access attack tries to gain access to a resource using a hijacked account or other means. Password attacks can be implemented by the use of brute-force attack methods Trojan horses or packet sniffers.
NIST Malware-as-a-Service Cyber Threat Alliance FortiGuard Labs Q3. Port redirection attack brute-force attack buffer overflow attack packet sniffer attack IP spoofing attack denial of service attack. Password attacks can be implemented.
Choose two Character mode provides users with administrative privilege EXEC access and requires use of the console vty or tty ports Packet mode provides remote users with access to network resources and requires use of dialup or VPN 8. Buffer overflow attacks write data beyond the allocated buffer memory to overwrite valid data or exploit systems to execute malicious code. ITC Final Exam Answers Which statement describes cybersecurity.
Which two statements characterize DoS attacks.
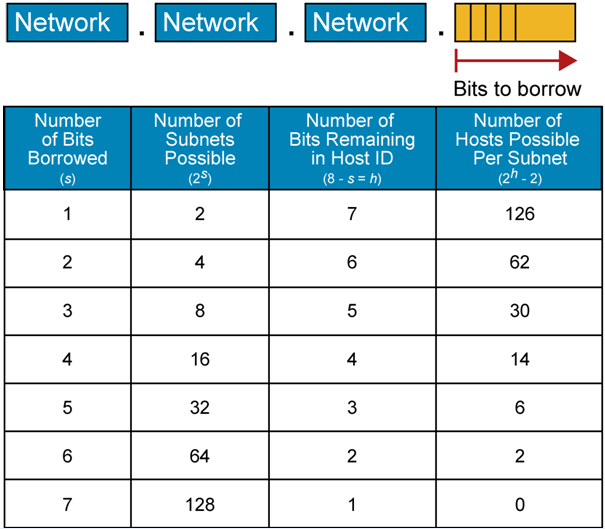
Ccna 1 V5 1 V6 0 Chapter 11 Exam Answers 2020 100 Full

Ccna 1 V5 1 V6 0 Chapter 11 Exam Answers 2020 100 Full
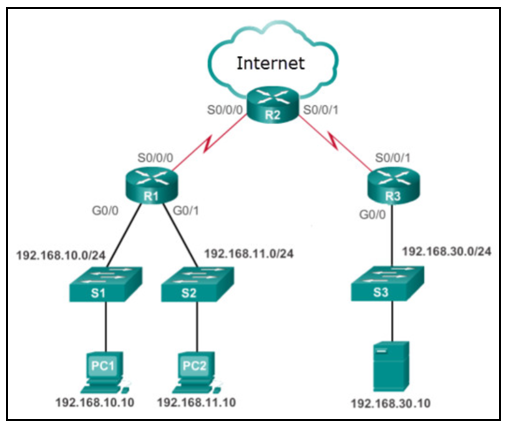
Ccna 3 V7 Modules 3 5 Network Security Exam Answers
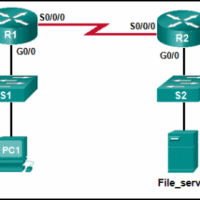
Modules 11 12 Network Infrastructure Security Group Exam Answers
Comments
Post a Comment